puppet系列(四)web+Passenger以及独立CA服务器提高性能
前三章主要记录了puppet的基础部分,这里结合实际生产环节记录一下puppet的集群技术。
一、puppet的纵向扩展
Phusion Passenger:
Phusion Passenger模块也被成为mod_rails、mod_passenger或者简称Passenger。Passenger是一个用于Ruby程序嵌入执行的Apache模块,由于它并不是apache的标准模块,所以需要独立的安装。puppet3已经去掉了对Mongel的支持,通过Passenger的方式可以提升master的处理瓶颈。
1.1 Apache+Passenger:
第一步:yum安装
#yum install ruby-devel ruby-libs rubygems libcurl-devel
#yum install httpd httpd-devel apr-util-devel apr-devel mod_ssl
#yum install gcc-c++ gcc openssl-devel
第二步:更换gem源来国内的源,因为国外的源经常被墙
#gem sources --add https://gems.ruby-china.org/ --remove https://rubygems.org/
# gem sources -l #查看一下剩下是不是换成国内的源了。 如果没有可以:# vim ~/.gemrc 这样手工更改
*** CURRENT SOURCES ***
https://gems.ruby-china.org/
第三步:gem安装必要的软件
#gem install rack -v 1.6.0 #gem跟yum不一样 要指定软件的版本。
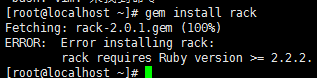
#不然就出现上面的报错:ERROR: Error installing rack: rack requires Ruby version >= 2.2.2. 会直接给你指定到最新版,并告诉你最新版是什么,然后需要对应的ruby版本。
#gem install rake -v 10.4.2
#gem install daemon_controller -v 1.2.0
#gem install passenger -v 4.0.56
第四步:解决相关依赖关系
#passenger-install-apache2-module #这里是一路回车啊,中间信息会很多,如果少yum了包的话,会提示你,所以要注意下。内容太多,下面是最后的输出部分。
And that's it! You may also want to check the Users Guide for security and optimization tips, troubleshooting and other useful information: /usr/lib/ruby/gems/1.8/gems/passenger-4.0.56/doc/Users guide Apache.html https://www.phusionpassenger.com/documentation/Users%20guide%20Apache.html Enjoy Phusion Passenger, a product of Phusion (www.phusion.nl) :-) https://www.phusionpassenger.com Phusion Passenger is a trademark of Hongli Lai & Ninh Bui.
# echo $? #最好测试一下是否有错误
0
博文来自:www.51niux.com
第五步:配置相关的文件和创建对应的目录
# cp /usr/share/puppet/ext/rack/example-passenger-vhost.conf /etc/httpd/conf.d/passenger.conf
下面是最后修改成型后的文件:
# cat /etc/httpd/conf.d/passenger.conf #这里是创建虚拟主机并加载passenger相关模块
LoadModule passenger_module /usr/lib/ruby/gems/1.8/gems/passenger-4.0.56/buildout/apache2/mod_passenger.so #加载passenger.so模块
<IfModule mod_passenger.c>
PassengerRoot /usr/lib/ruby/gems/1.8/gems/passenger-4.0.56/
PassengerRuby /usr/bin/ruby #配置passenger来使系统的ruby解释器
PassengerHighPerformance on
PassengerMaxPoolSize 12
PassengerPoolIdleTime 1500
PassengerStatThrottleRate 120
</IfModule>
Listen 8140 #虚拟主机配置apache来监听在8140端口,并且使用SSL和puppet master生成的证书对所有通讯进行加密。
<VirtualHost *:8140> #配置虚拟主机并开启apache的ssl引擎
SSLEngine on
SSLProtocol ALL -SSLv2 -SSLv3
SSLCipherSuite EDH+CAMELLIA:EDH+aRSA:EECDH+aRSA+AESGCM:EECDH+aRSA+SHA384:EECDH+aRSA+SHA256:EECDH:+CAMELLIA256:+AES256:+CAMELLIA128:+AES128:+SSLv3:!aNULL:!eNULL:!LOW:!3DES:!MD5:!EXP:!PSK:!DSS:!RC4:!SEED:!IDEA:!ECDSA:kEDH:CAMELLIA256-SHA:AES256-SHA:CAMELLIA128-SHA:AES128-SHA
SSLHonorCipherOrder on
SSLCertificateFile /var/lib/puppet/ssl/certs/master.puppet.pem #这些服务器端自己的证书文件路径都要是正确的。
SSLCertificateKeyFile /var/lib/puppet/ssl/private_keys/master.puppet.pem
SSLCertificateChainFile /var/lib/puppet/ssl/ca/ca_crt.pem
SSLCACertificateFile /var/lib/puppet/ssl/ca/ca_crt.pem
SSLCARevocationFile /var/lib/puppet/ssl/ca/ca_crl.pem #打开证书撤销功能,当我们颁发或撤销Puppet agent的证书时,Puppet cert命令会自动更关心ca_crl.pem文件
SSLVerifyClient optional
SSLVerifyDepth 1
SSLOptions +StdEnvVars +ExportCertData #配置Apache来验证Puppet agent证书的真实性。验证的结果会被保存在这个环境变量中,运行在Passenger中的Puppet master进程会使用这个变量来认证Puppet agent。
RequestHeader unset X-Forwarded-For #Puppet agent证书验证的结果会以客户端请求头的形式存放在标准环境中。
#设置访问的头文件
RequestHeader set X-SSL-Subject %{SSL_CLIENT_S_DN}e
RequestHeader set X-Client-DN %{SSL_CLIENT_S_DN}e
RequestHeader set X-Client-Verify %{SSL_CLIENT_VERIFY}e
DocumentRoot /etc/puppet/rack/public/
RackBaseURI /
#指定rack配置的目录,并设置目录的访问权限。提供rack配置文件config.ru的路径。
<Directory /etc/puppet/rack/>
Options None
AllowOverride None
Order allow,deny
allow from all
</Directory>
ErrorLog "/var/log/puppet_error.log"
ServerSignature Off
CustomLog "/var/log/puppet_access.log" combined # 设置Puppet访问日志(可选,默认日志为other_vhosts_access.log)
</VirtualHost># service httpd configtest #检查配置文件是否有问题
Syntax OK
#mkdir /etc/puppet/rack/{public,tmp} #为Rack和Puppet master的rack程序实例创建框架目录。
#cp /usr/share/puppet/ext/rack/config.ru /etc/puppet/rack/ #配置文件保持默认不需要修改
#chown -R puppet:root /etc/puppet/rack #设置目录权限
第六步:服务做操作
# service puppetmaster stop #关闭puppetmaster服务
# chkconfig puppetmaster off #禁止开机启动,防止抢占apache的监听的8140端口
# /etc/init.d/httpd restart #重启apache服务
# chkconfig httpd on #添加开机启动
博文来自:www.51niux.com
第七步:测试
# netstat -lntup|grep 8140 #服务端查看此服务已经启动
tcp 0 0 :::8140 :::* LISTEN 10112/httpd
浏览器测试:链接地址为:https://puppet服务端的IP或者域名:8140
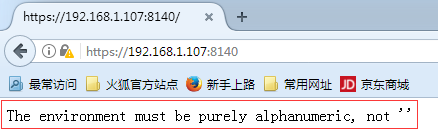
#当页面出现下面的一串字的时候说明安装成功了:
The environment must be purely alphanumeric, not ''
注:
如果是新的puppet服务端,并且没有做DNS服务验证的话,千万不要忘记再/etc/hosts里面加上自己服务端相关的解析,不然会有下面的报错,并且重启httpd服务你也会发现不生效。
# tail -f /var/log/puppet_error.log
[Wed Apr 26 17:10:49 2017] [warn] RSA server certificate CommonName (CN) `master.puppet' does NOT match server name!?
客户端测试:
找一个新的客户端执行:# puppet agent -t #查看是否能申请到证书,再服务器端开启证书自动签名的情况下
服务端日志查看:
# tail -f /var/log/httpd/ssl_access_log
192.168.1.106 - - [26/Apr/2017:18:13:48 +0800] "GET /production/node/192.168.1.106?transaction_uuid=35b49a5b-47a1-44fd-b190-aa15bdc200c0&fail_on_404=true HTTP/1.1" 200 4752 "-" "Ruby" 192.168.1.106 - - [26/Apr/2017:18:13:48 +0800] "GET /production/file_metadatas/pluginfacts?links=manage&recurse=true&ignore=.svn&ignore=CVS&ignore=.git&checksum_type=md5 HTTP/1.1" 200 283 "-" "Ruby" 192.168.1.106 - - [26/Apr/2017:18:13:48 +0800] "GET /production/file_metadatas/plugins?links=manage&recurse=true&ignore=.svn&ignore=CVS&ignore=.git&checksum_type=md5 HTTP/1.1" 200 283 "-" "Ruby" 192.168.1.106 - - [26/Apr/2017:18:13:50 +0800] "POST /production/catalog/192.168.1.106 HTTP/1.1" 200 574 "-" "Ruby" 192.168.1.106 - - [26/Apr/2017:18:13:50 +0800] "PUT /production/report/192.168.1.106 HTTP/1.1" 200 9 "-" "Ruby"
#服务器端上面查看返回的也全是200的日志信息。
至此,我们关于apache+Passenger的操作,已经操作完毕了。以后再修改puppet服务里面的配置啊,需要重启服务了,就直接:# /etc/init.d/httpd restart,就不要再去重启puppetmaster服务了。
1.2 Nginx+Passenger:
第一步:yum安装相关软件包
# yum install gcc gcc-c++ curl-devel openssl-devel zlib-devel ruby-devel rubygems -y
第二步:更换gem源来国内的源,因为国外的源经常被墙
#gem sources --add https://gems.ruby-china.org/ --remove https://rubygems.org/
# gem sources -l #查看一下剩下是不是换成国内的源了。 如果没有可以:# vim ~/.gemrc 这样手工更改
*** CURRENT SOURCES ***
https://gems.ruby-china.org/
第三步:gem安装必要的软件
#gem install rack -v 1.6.0 #gem跟yum不一样 要指定软件的版本。

#不然就出现上面的报错:ERROR: Error installing rack: rack requires Ruby version >= 2.2.2. 会直接给你指定到最新版,并告诉你最新版是什么,然后需要对应的ruby版本。
#gem install rake -v 10.4.2
#gem install daemon_controller -v 1.2.0
#gem install passenger -v 4.0.56
第四步:解决相关依赖关系
# passenger-install-nginx-module #自动完成整个passenger配置流程。运行过程它会提示以下两步。步骤1自动下载nginx安装(推荐),步骤二通过已经有的nginx来安装passenger。
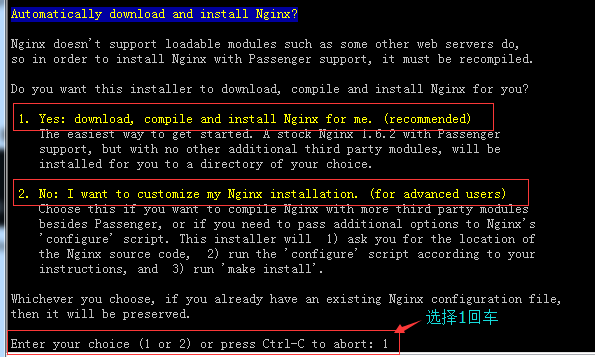
#但是呢很多时候可能会因为网络原因,下载比较慢而导致下载失败,你可以提前把下载好的nginx的tar包放/tmp目录下面。如:#cd /tmp && wget http://www.nginx.org/download/nginx-1.6.2.tar.gz
还有一个地方可以选择一下:
Where do you want to install Nginx to?
Please specify a prefix directory [/opt/nginx]: /usr/local/nginx #让选择nginx的安装路径
还是当出现下面的段落的时候表示安装成功:
And that's it! You may also want to check the Users Guide for security and optimization tips and other useful information: /usr/local/lib/ruby/gems/2.2.0/gems/passenger-4.0.56/doc/Users guide Nginx.html https://www.phusionpassenger.com/documentation/Users%20guide%20Nginx.html Enjoy Phusion Passenger, a product of Phusion (www.phusion.nl) :-) https://www.phusionpassenger.com Phusion Passenger is a trademark of Hongli Lai & Ninh Bui.
第五步:创建rack所需要的配置文件与目录:
#mkdir /etc/puppet/rack/{public,tmp} -p #为Rack和Puppet master的rack程序实例创建框架目录。
#cp /usr/share/puppet/ext/rack/config.ru /etc/puppet/rack/ #配置文件保持默认不需要修改
#chown -R puppet:root /etc/puppet/rack #设置目录权限
第六步:修改nginx的配置文件:
# cat /usr/local/nginx/conf/nginx.conf|grep -v "#"|grep -v "^$"
worker_processes 4;
events {
worker_connections 1024;
}
http {
passenger_root /usr/lib/ruby/gems/1.8/gems/passenger-4.0.56; #指定passenger的root目录,可以使用# passenger-config --root得到
passenger_ruby /usr/bin/ruby; #指定ruby命令的执行路径。ruby最好是yum安装的,不要编译安装容易出现未知错误。
include mime.types;
default_type application/octet-stream;
sendfile on;
keepalive_timeout 65;
server {
listen 80;
server_name localhost;
location / {
root html;
index index.html index.htm;
}
error_page 500 502 503 504 /50x.html;
location = /50x.html {
root html;
}
}
server {
listen 8140 ssl; #由于puppet通信使用的是ssl,所以此处必须定义ssl
server_name master.puppet 192.168.1.112; #puppet服务器的主机名,我这里新找了台主机
passenger_enabled on;
#设置HTTP头用于验证CA
passenger_set_cgi_param HTTP_X_CLIENT_DN $ssl_client_s_dn; #标记client请求时提供的dn和VERIFY,用于传递到puppet
passenger_set_cgi_param HTTP_X_CLIENT_VERIFY $ssl_client_verify;
#开启nginx日志。通过日志监控nginx服务器的健康状态。
access_log /usr/local/nginx/puppet_access.log;
error_log /usr/local/nginx/puppet_error.log;
root /etc/puppet/rack/public; #nginx和passenger的协作目录
#设置puppet证书文件地址
ssl_certificate /var/lib/puppet/ssl/certs/master.hadoop.pem;
ssl_certificate_key /var/lib/puppet/ssl/private_keys/master.hadoop.pem;
ssl_crl /var/lib/puppet/ssl/ca/ca_crl.pem;
ssl_client_certificate /var/lib/puppet/ssl/certs/ca.pem;
ssl_ciphers SSLv2:-LOW:-EXPORT:RSA;
ssl_prefer_server_ciphers on;
ssl_verify_client optional;
ssl_verify_depth 1;
ssl_session_cache shared:SSL:128m;
ssl_session_timeout 5m;
}
}第七步、启动相关服务并测试:
# /etc/init.d/puppetmaster stop
# /usr/local/nginx/sbin/nginx
# netstat -lntup|grep 8140
tcp 0 0 0.0.0.0:8140 0.0.0.0:* LISTEN 14198/nginx
浏览器访问:
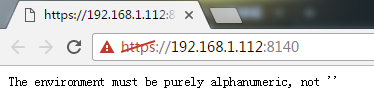
客户端访问:#puppet agent -t
服务器端查看:
# puppet cert list -all #多了一个192.168.1.113,说明已经成功了。
+ "192.168.1.113" (SHA256) 0C:18:C7:57:9F:58:FB:14:43:E0:45:45:1C:CB:57:EA:D8:0E:8F:93:8B:36:D0:5C:42:83:8A:74:10:15:76:54
+ "master.hadoop" (SHA256) A9:A0:C5:51:EE:D9:03:68:17:6A:7C:01:55:B4:21:4F:74:D3:6A:62:4F:46:CB:28:E5:D4:34:9E:2F:95:EE:86
# tail -f /var/log/puppet_access.log #日志查看http状态码全是200也是OK的。
192.168.1.113 - - [26/Apr/2017:23:49:07 +0800] "GET /production/node/192.168.1.113?fail_on_404=true&transaction_uuid=be9f7755-be3d-41ae-be99-1fe4fd395127 HTTP/1.1" 200 4286 "-" "-"
192.168.1.113 - - [26/Apr/2017:23:49:07 +0800] "GET /production/file_metadatas/pluginfacts?recurse=true&checksum_type=md5&links=manage&ignore=.svn&ignore=CVS&ignore=.git HTTP/1.1" 200 283 "-" "-"
192.168.1.113 - - [26/Apr/2017:23:49:07 +0800] "GET /production/file_metadatas/plugins?recurse=true&checksum_type=md5&links=manage&ignore=.svn&ignore=CVS&ignore=.git HTTP/1.1" 200 283 "-" "-"
192.168.1.113 - - [26/Apr/2017:23:49:07 +0800] "POST /production/catalog/192.168.1.113 HTTP/1.1" 200 574 "-" "-"
192.168.1.113 - - [26/Apr/2017:23:49:07 +0800] "PUT /production/report/192.168.1.113 HTTP/1.1" 200 9 "-" "-"
注:
ssl_ciphers SSLv2:-LOW:-EXPORT:RSA;已经不是ssl_ciphers SSLv2:-LOW:-EXPORT:RC4+RSA; 没有RC4协议了,因为已经是浏览器不支持的协议了,如果你加了此协议的话,访问浏览器(当然对puppet客户端的访问是不受影响的):

博文来自:www.51niux.com
二、puppet横向扩展
2.1 独立CA认证服务器
2.1.1 CA服务器上面的操作:
第一步:yum安装
# yum install puppet puppet-server facter -y
第二步:同步时间、做hosts设置
# cat /etc/hosts
192.168.1.107 master.puppet
192.168.1.106 ca.puppet
第三步:证书认证
# puppet cert --generate --dns_alt_names puppetca ca.puppet #使用puppet cert命令生成CA服务器。生成ca.puppet域名授权证书文件,前面是证书别名,后面是证书名称。
Notice: Signed certificate request for ca
Notice: ca.puppet has a waiting certificate request
Notice: Signed certificate request for ca.puppet
Notice: Removing file Puppet::SSL::CertificateRequest ca.puppet at '/var/lib/puppet/ssl/ca/requests/ca.puppet.pem'
Notice: Removing file Puppet::SSL::CertificateRequest ca.puppet at '/var/lib/puppet/ssl/certificate_requests/ca.puppet.pem'
# puppet cert --generate --dns_alt_names puppetmaster master.puppet #使用puppet cert命令生成master服务器证书认证。
Notice: master.puppet has a waiting certificate request
Notice: Signed certificate request for master.puppet
Notice: Removing file Puppet::SSL::CertificateRequest master.puppet at '/var/lib/puppet/ssl/ca/requests/master.puppet.pem'
Notice: Removing file Puppet::SSL::CertificateRequest master.puppet at '/var/lib/puppet/ssl/certificate_requests/master.puppet.pem'
第四步:验证证书是否生成
# puppet cert --list --all
+ "ca.puppet" (SHA256) BD:54:F2:6A:B2:28:F8:B9:B3:4C:CC:49:D6:F9:42:17:97:AA:B1:22:9B:DB:58:48:3B:55:97:6E:BD:03:D6:9B (alt names: "DNS:ca.puppet", "DNS:puppetca")
+ "master.puppet" (SHA256) 2F:5F:93:04:38:C8:4E:B2:D9:66:38:EF:5D:46:BE:87:97:A4:BD:6E:1D:EC:83:60:A1:AD:1A:A0:F3:70:B4:0D (alt names: "DNS:master.puppet", "DNS:puppetmaster")
第五步:配置CA证书上面的配置文件
# cat /etc/puppet/puppet.conf #添加[master]标签
[master]
confdir = /etc/puppet
certname = ca.puppet
ca = true
第六步:启动服务
# service puppetmaster restart #在CA服务器上面启动puppetmaster服务
# chkconfig puppetmaster on #添加开机启动,如果是Centos7的系统就是:systemctl enable puppetmaster.service
2.1.2 puppet master服务器上面的操作:
第一步:yum软件并且时间同步并添加hosts文件
# cat /etc/hosts
192.168.1.107 master.puppet
192.168.1.106 ca.puppet
第二步:创建证书目录,如果不存在的话:
# mkdir /var/lib/puppet/ssl/{certs,ca,private_keys} -p
第三步:将puppetca上生成的puppetmaster公钥、私钥和根证书复制到master服务器
#scp -r root@192.168.1.106:/var/lib/puppet/ssl/ca/signed/master.puppet.pem /var/lib/puppet/ssl/certs/
#scp -r root@192.168.1.106:/var/lib/puppet/ssl/ca/ca_crt.pem /var/lib/puppet/ssl/certs/
#scp -r root@192.168.1.106:/var/lib/puppet/ssl/private_keys/master.puppet.pem /var/lib/puppet/ssl/private_keys/master.puppet.pem
#scp -r root@192.168.1.106:/var/lib/puppet/ssl/ca/ca_crl.pem /var/lib/puppet/ssl/ca/ca_crl.pem
第四步:更改服务端配置文件
# cat /etc/puppet/puppet.conf
[master]
ca = false #关闭master的ca认证服务
[agent] #增加agent标签,增加server和ca_server字段
server = master.puppet
ca_server = ca.puppet
第五步:重启服务并验证
# service puppetmaster restart
# puppet agent -t #因为已经认证过的证书发过来了了,所以不会再有证书认证下发的过程了。
Info: Retrieving pluginfacts
Info: Retrieving plugin
Info: Caching catalog for master.puppet
Info: Applying configuration version '1493280377'
Notice: Finished catalog run in 0.03 seconds
2.1.3 客户端上面的操作:
第一步:yum软件包,时间同步并添加hosts文件:
# cat /etc/hosts
192.168.1.107 puppet.master
192.168.1.106 ca.puppet
第二步:修改配置文件:
# cat /etc/puppet/puppet.conf
[main]
logdir = /var/log/puppet
rundir = /var/run/puppet
ssldir = $vardir/ssl
[agent]
certname = 192.168.1.105
daemonize = true
allow_duplicate_certs = true
report = true
reports = store,http
report_server = master.puppet
runinterval = 9000m
configtimeout = 2m
color = ansi
ignorecache = true
classfile = $vardir/classes.txt
ocalconfig = $vardir/localconfig
server = master.puppet
ca_server = ca.puppet
第三步:申请证书认证:
# puppet agent -t
Exiting; no certificate found and waitforcert is disabled #这表示已经连接成功,但是就没有将证书下发下来。
2.1.4 CA服务器上面的再次操作:
第一步(一开始没改成自动签发证书,是为了要验证一下):
# puppet cert list -all #查看有一个105的证书再申请完成认证
"192.168.1.105" (SHA256) 63:F8:D1:42:73:93:EF:EE:1B:1D:0D:AA:B3:EA:69:B9:8D:00:AB:71:FB:CC:06:90:F4:CF:34:BE:0F:CC:80:9E
# puppet cert --sign 192.168.1.105 #给192.168.1.105认证,客户端再次#puppet agent -t是认证成功的。
第二步:修改为自动签发证书
# cat /etc/puppet/puppet.conf #这是最后的配置文件,开启了自动签发证书。
[main]
logdir = /var/log/puppet
rundir = /var/run/puppet
ssldir = $vardir/ssl
[agent]
classfile = $vardir/classes.txt
localconfig = $vardir/localconfig
server = master.puppet
ca_server = ca.puppet
[master]
autosign = true
autosign = /etc/puppet/autosign.conf
confdir = /etc/puppet
certname = ca.puppet
ca = true
# echo "*" >/etc/puppet/autosign.conf #并且创建此文件
你可以再搞些新的客户端来进行证书的认证,并可以在服务器端进行一些资源的配置,看客户端是否能顺利执行。
另外我们前面不是记录了Apache+Passenger,如果我们的puppet master服务器做了passenger优化,那么web配置文件要进行更改了,更改如下:
# cat /etc/httpd/conf.d/passenger.conf #就是确保几个证书文件的位置正确
SSLCertificateFile /var/lib/puppet/ssl/certs/master.puppet.pem
SSLCertificateKeyFile /var/lib/puppet/ssl/private_keys/master.puppet.pem
SSLCertificateChainFile /var/lib/puppet/ssl/certs/ca_crt.pem
SSLCACertificateFile /var/lib/puppet/ssl/certs/ca_crt.pem
SSLCARevocationFile /var/lib/puppet/ssl/ca/ca_crl.pem
# /etc/init.d/httpd restart #然后再重启下apache服务。
2.1.5 小结
至此ca做独立服务器的设置已经记录完毕。
puppet CA证书迁移出去后,需要做负载均衡或者主备,来以防止CA服务器挂掉而导致puppet的master端和agent端不能进行证书认证,而导致主机管理操作不能完成。把CA证书颁发和认证剥离出去,可以提高puppet服务器的处理效率。还可以通过DNS智能解析技术,在多机房设置CA证书服务器,然后根据来源IP做DNS解析调度,调度到客户端本机房的CA服务器或者距离较近的CA服务器。这样一搞的话,puppet服务器所需要的服务器的数量将成倍增长。
当然什么样的架构都根据实际规模来的,如果机器过少的话不推荐这种架构,很浪费主机资源。
如果数量比较少的话,可以采取puppet服务端还是继续和CA服务绑定再一起的操作,但是加上我们上面说的垂直扩展,然后在puppet服务器端前面做负载均衡调度,然后ca证书放到一个共享存储,然后再加一个文件服务器,所有的文件都从哪个文件服务器来获取,puppet服务端只是用来发布命令,这样一个垂直加横向的架构,对于我们之前近千台服务器规模的场景,应用的还是很顺畅的。
